In this article, we explore the security challenges faced by Web3 projects due to their dependence on centralized cloud infrastructure providers like AWS, GCP, and Alibaba Cloud. By leveraging our expertise in web3 security, cloud security, and previous audits/pentests, we offer an in-depth understanding of Web3 security in the context of cloud infrastructure. We examine the paradox of centralized decentralization, where Web3 projects pursue decentralization while relying on centralized cloud providers.
I. State Of The Art
The Web3 economy, built on the principles of decentralization, is facing a paradoxical challenge when it comes to cloud infrastructure. Although the decentralized nature of Web3 is designed to prevent centralization and single points of failure, for now, it heavily relies on centralized cloud infrastructure providers, such as Amazon Web Services (AWS), Google Cloud Platform (GCP), or Alibaba Cloud, to run its nodes, servers, and internal infrastructure.
For instance, a typical Web3 company might have:
- A GitHub repository,
- A Google Workspace collaborative space,
- A dApp hosted on DigitalOcean,
- Nodes and infrastructure elements in AWS.
Given that 65.27% of Ethereum nodes are hosted in the cloud, as reported by ethernodes.org, it is crucial to audit the cloud infrastructure hosting Web3 projects.
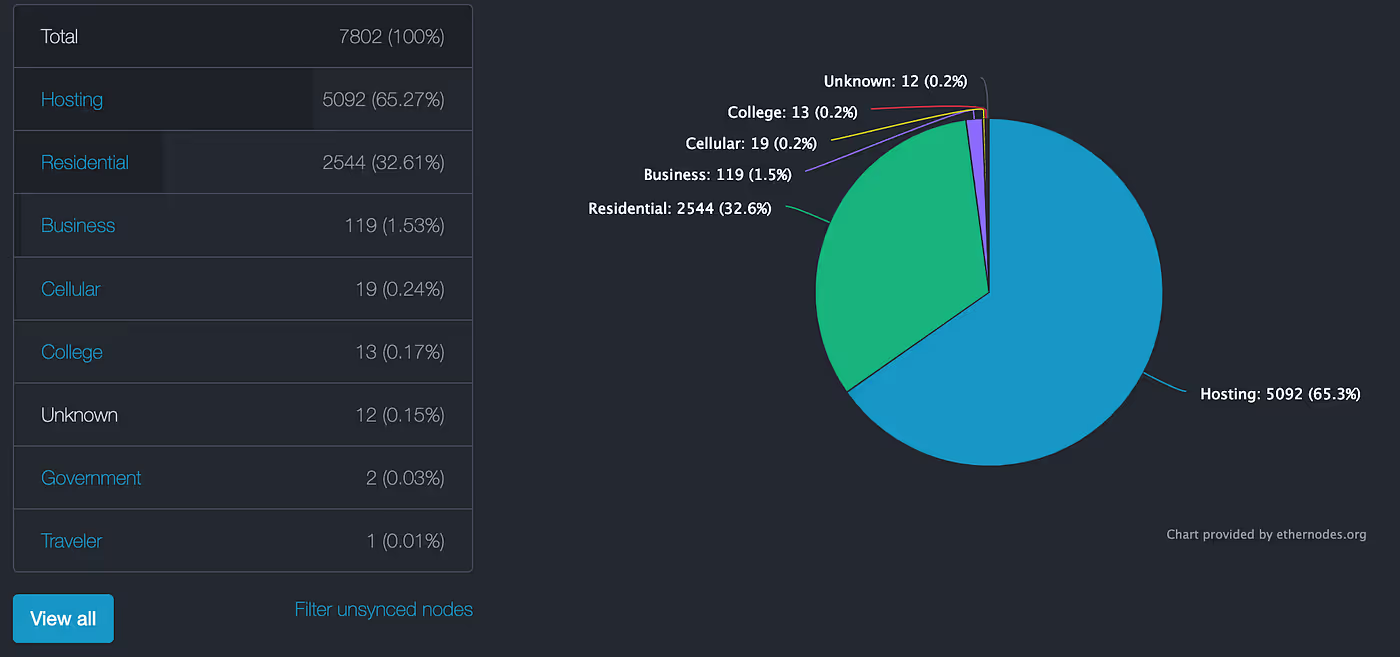
A snapshot taken on April 18, 2019, shows that Ethereum nodes are run on various cloud hosting platforms, with AWS being the most popular provider, accounting for 24.6% of the total share.
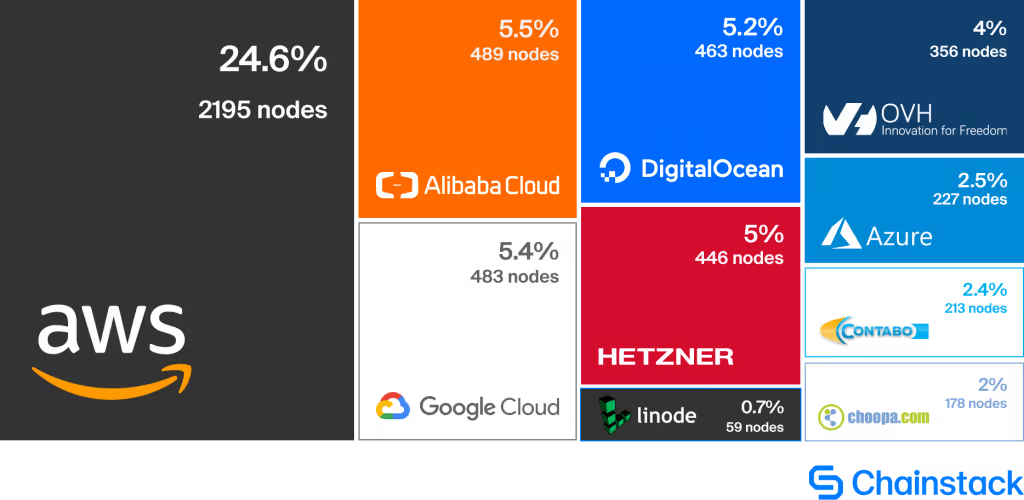
As of 20 April 2023, it can be seen that AWS has collected a large share of the market for node hosting.
Indeed, 61.04% of nodes are at this date hosted on AWS according to ethernodes.org:
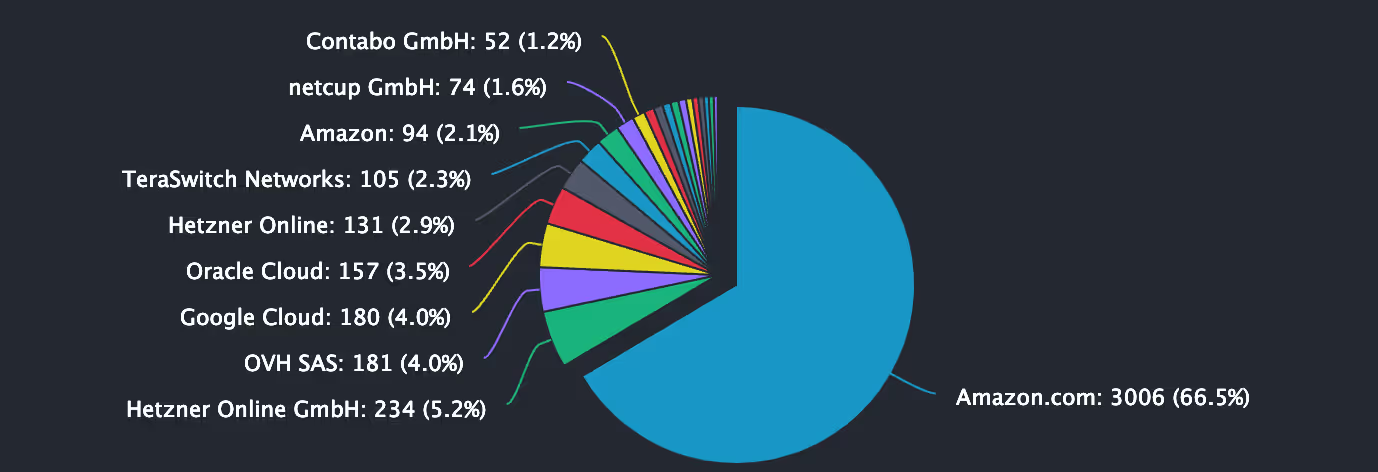
While it may be convenient for Web3 developers to set up nodes on cloud servers instead of buying and maintaining their own hardware, it comes at a cost to decentralization.
NFT Case Example
It should be noted that the data for most NFTs are not stored on-chain, as this would prove to be prohibitively expensive for a majority of image-based NFTs.
In every NFT on-chain storage, a URL is incorporated that points to the relevant data. Upon examining numerous NFTs available on popular marketplaces, some of which are valued at tens, hundreds, or even millions of dollars, it was observed that the URLs frequently lead to a basic VPS running Apache on a Cloud provider like Amazon or Google. Consequently, any individual with access to the server, subsequent domain name owners, or those who compromise the server can alter various aspects of the NFT, including the image, title, and description, at any given time, irrespective of token ownership.
Source: Siddharth Gowda, “NFTs, Data Ownership and Decentralized Metadata”:
II. The Cloud: An attack vector and a service interruption vector for web3 projects
Web3 is only as decentralized as its supporting infrastructure, and the centralization of most cloud computing and data storage infrastructures creates cloud and web vulnerabilities for Web3 applications.
Interruption vector example
For instance, service interruptions like the Infura outage, which caused Coinbase Wallet and Binance to cease ETH and ERC20 token withdrawals, demonstrate the risks of relying on centralized suppliers.
Coinmarketcap article: https://coinmarketcap.com/alexandria/article/ethereums-infura-iating-outage-revives-decentralization-concerns?source=post_page-----13c246c1155e---------------------------------------
Gabby Dizon, the CEO of Yield Guild Games, a play-to-earn gaming platform, added that cloud infrastructure security is a critical issue for Web3 projects, especially those that deal with high-value assets. He noted that Web3 projects need to work with reputable cloud providers and ensure that their cloud infrastructure is secure and compliant with industry standards.
Web3 projects also need to audit their cloud infrastructure to ensure that it is secure and complies with industry standards. We noted that while Web3 projects may focus on auditing their smart contracts, they also need to audit their cloud infrastructure to ensure that it is secure and not vulnerable to attacks.
Attack scenario
- Reconnaissance
The attacker gathers information about the Web3 project’s team members from social media, forums, and other public sources to create a list of targets. This includes developers, system administrators, and management personnel who may have privileged access to AWS resources. - Crafting the Phishing Campaign
The attacker creates a highly targeted and convincing phishing campaign, designed to trick the victims into clicking on a malicious link or providing their AWS credentials. This may involve impersonating a legitimate company or individual, using a similar domain or email address, and crafting a believable message that prompts the target to take a specific action, such as logging into a fake AWS management console. - Credential Theft
When the victim clicks on the malicious link or enters their AWS credentials on the fake login page, the attacker captures the provided information.
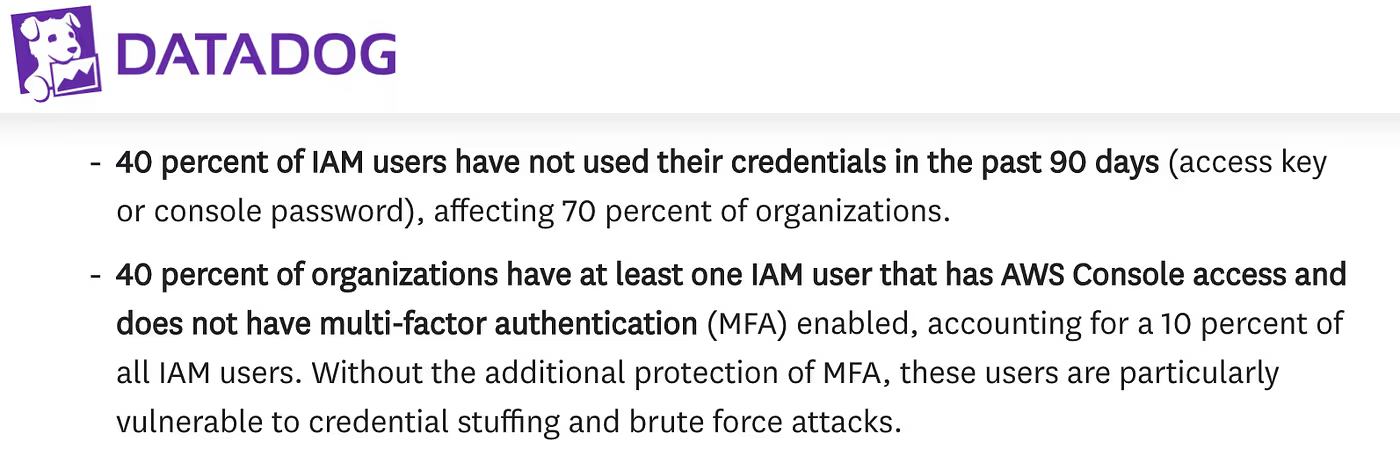
– Using the stolen credentials, the attacker gains initial access to the AWS environment, as we often notice during our audits that users with access to the AWS web console do not have an enabled MFA. According to Datadog, and its “State of AWS security” study:
- Privilege Escalation
The attacker starts exploring the compromised AWS environment, looking for IAM policies assigned to the compromised user. Indeed, the account has wide-ranging IAM policies, which would make it significantly easier for the attacker to escalate their privileges, giving them more control over AWS resources.
– For instance, in one of our audits, we were able to detect an AWS role attached to all developers in the account with the following policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
]
}
- Lateral Movement
With elevated privileges, the attacker can now move laterally within the AWS environment, looking for sensitive information, such as API keys, private keys, or access to other services (such as databases or message queues). They may also search for weaknesses in the infrastructure, such as misconfigured S3 buckets or exposed services. - Exploitation
Once the attacker has gained a deeper understanding of the Web3 project’s infrastructure, they can exploit identified vulnerabilities to manipulate transactions, exfiltrate sensitive data, or cause disruption to the project.
Conclusion
Web3 space is not yet ready for complete decentralization. For now, the paradox of centralized decentralization in cloud providers highlights that projects must rely on a mix of decentralized and centralized infrastructure to ensure the security and availability of their systems. While this may not be the ideal solution, it is a necessary step in the development of the Web3 ecosystem.
At the end, Web3 projects must audit not only their smart contracts but also their cloud infrastructure that hosts their projects. While decentralized infrastructure providers offer promise for the future.
About the Author:
Ilan Abitbol is a cybersecurity expert and a member of the Resonance Security team, specializing in web3 security and cloud infrastructure audits.
Sources:
[2] https://www.datacenterknowledge.com/amazon/aws-outage-data-centers-fail-serve-us-east-customers
[3] https://chainstack.com/the-ethereum-cloud-vs-on-premises-nodes-conundrum/
[4] https://www.coindesk.com/filecoin-ico-257-million
[5] https://vedangvats.com/web3-can-only-be-as-decentralized-as-its-supporting-infrastructure/


.avif)













.png)