Salesforce is the beating heart of many organizations’ customer operations. For attackers, that heart is a gold mine. This year, we’ve watched one of the most coordinated, successful SaaS-targeted campaigns in recent history, and Salesforce customers are bleeding data like a severed artery.
We’re not talking about a single breach, my friends. We’re talking Google, Adidas, Allianz, LVMH, Pandora, Coca-Cola, and more, all compromised in the same campaign pattern.
Different brands, same vector, same failure: trusting a third-party SaaS with your crown jewels without a strong security chokehold.
The Hit List: 2025’s Salesforce-Linked Breaches
Let’s connect the dots, because the attackers sure did!
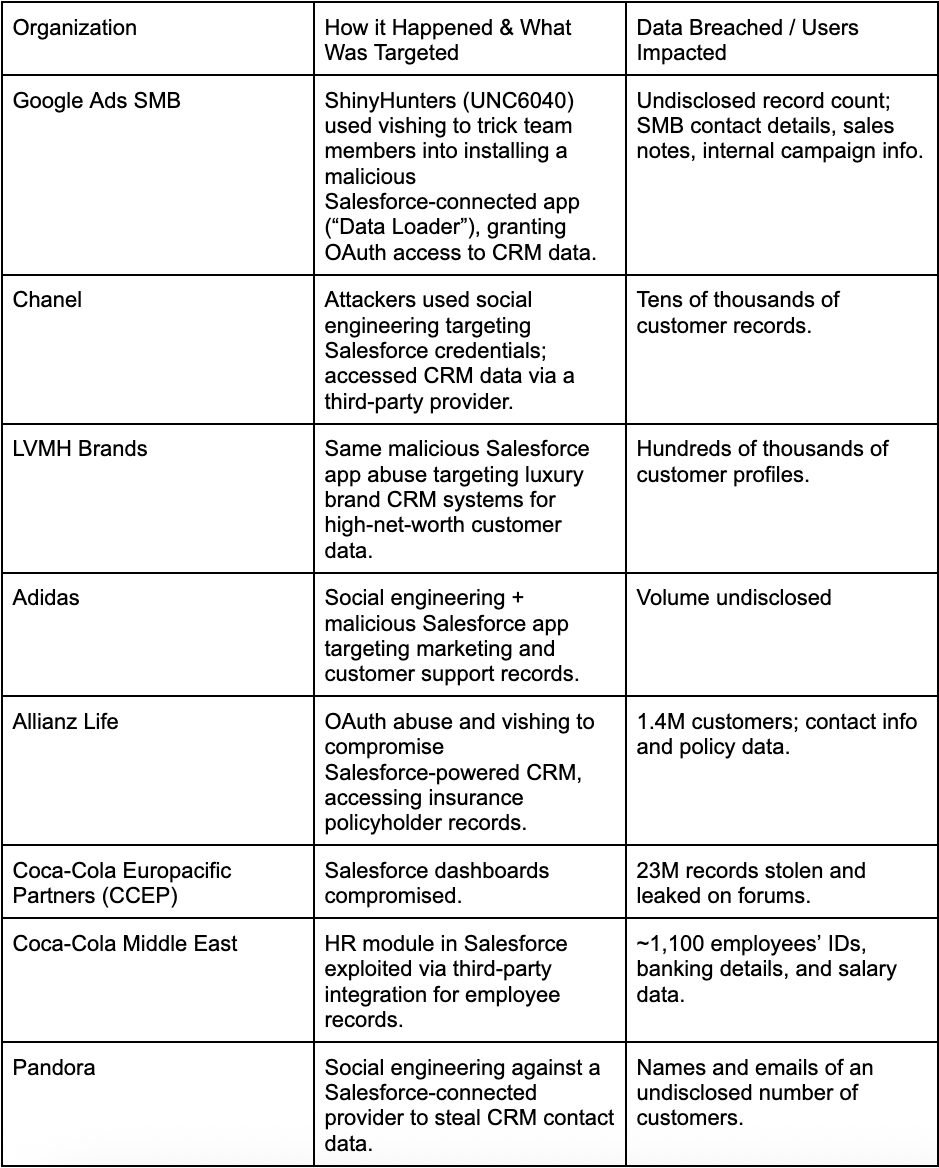
[A summary table of these hacks is attached at the end of this section.]
Google Ads SMB Data Breach
How did it happen & what was targeted?
ShinyHunters (UNC6040) used vishing to trick Google Ads SMB team members into installing a malicious Salesforce-connected app disguised as “Data Loader.” This granted OAuth access to Salesforce CRM data.
Amount of data breached & users impacted?
Undisclosed record count; involved small and medium business contact details, sales notes, and internal campaign info.
Chanel
How did it happen & what was targeted?
Attackers accessed a database hosted by a third-party CRM provider and exfiltrated limited U.S. customer data, including names, email addresses, phone numbers, and mailing addresses, for individuals who had contacted the client care center. While the breach stemmed from social engineering targeting Salesforce credentials, no breach of the Salesforce platform itself occurred.
Amount of data breached & users impacted?
Tens of thousands (estimated figure) of customer records with names, emails, mailing addresses, and phone numbers. No payment data reported stolen.
LVMH Brands (Louis Vuitton, Dior, Tiffany & Co.)
How did it happen & what was targeted?
Attackers started with highly targeted vishing calls to customer service and marketing teams across multiple LVMH subsidiaries. Impersonating internal IT support, they instructed employees to “update” or “reconnect” a Salesforce Data Loader app, which in reality was a malicious connected app under attacker control. Once OAuth access was granted, the attackers were able to bypass MFA and inherit the victim’s full Salesforce permissions.
Amount of data breached & users impacted?
Exact figures undisclosed; estimated hundreds of thousands of customer profiles across multiple brands.
Adidas
How did it happen & what was targeted?
Attackers posed as Salesforce technical support, and they convinced staff to authorize a fraudulent connected app, disguised as a legitimate CRM utility, within the company’s Salesforce environment. This malicious app was granted OAuth access, bypassing multi-factor authentication and inheriting all associated user privileges. Once embedded, the attackers initiated bulk API calls to extract CRM datasets.
Amount of data breached & users impacted?
Volume not disclosed; potentially tens of thousands of customer entries exposed.
Allianz Life
How did it happen & what was targeted?
Threat actors began by targeting Allianz Life employees with tailored vishing calls posing as internal IT or Salesforce support staff. These calls convinced staff to authorize a malicious connected app disguised as a legitimate Salesforce integration tool. Once granted OAuth access, the attackers bypassed MFA entirely and inherited the permissions of the compromised users. The malicious app was then used to systematically query Allianz’s Salesforce-powered CRM, which contained highly sensitive insurance policyholder data.
Amount of data breached & users impacted?
1.4 million customers affected; details include contact information and policy data.
Coca-Cola Europacific Partners (CCEP)
How did it happen & what was targeted?
Attackers disguised as internal IT or Salesforce support and guided victims into authorizing a malicious connected app masquerading as a legitimate Salesforce analytics or reporting tool. Once OAuth access was granted, the attackers sidestepped MFA and gained full API-level access to CCEP’s Salesforce environment.
Amount of data breached & users impacted?
23 million records were stolen and later leaked on public forums.
Coca-Cola Middle East
How did it happen & what was targeted?
Attackers targeted HR and administrative staff who managed employee data through a Salesforce-integrated human resources platform. By impersonating Salesforce technical support, they convinced staff to authorize a malicious connected app disguised as an “HR data sync” or “compliance update” tool. With OAuth access secured, the attackers bypassed MFA and tapped directly into the HR module hosted within Salesforce.
Amount of data stolen & users impacted?
~1,100 employees’ IDs, banking details, and salary data.
Pandora
How did it happen & what was targeted?
Attackers targeted a third-party service provider that managed Pandora’s Salesforce environment. Through a series of convincing vishing calls, threat actors impersonated Salesforce or IT support, persuading staff to authorize a fraudulent connected app disguised as a legitimate CRM utility. Once OAuth access was granted, they bypassed MFA and executed API queries to pull customer records from the Salesforce database.
Amount of data breached & users impacted?
Names and emails of an undisclosed number of customers.
Quick summary table:
Spotlight on ShinyHunters
Let’s get tactical about the suspected mastermind behind the majority of these attacks: ShinyHunters (formally UNC6040 for intrusion, UNC6240 for extortion).
- Who they are: A financially motivated cybercrime gang infamous for high-profile breaches (e.g., AT&T, Santander, Ticketmaster). Since 2025, they’ve systematically targeted enterprise Salesforce CRM systems using low-tech social engineering, specifically, vishing and malicious OAuth-connected apps.
- Their playbook:
- Voice phishing (vishing) to trick employees into granting access via a fake connected app (often masquerading as Salesforce Data Loader).
- Generate OAuth tokens with excessive scope, bypassing MFA and permissions.
- Exfiltrate CRM data, often customer contact details or sales records.
- Demand ransom or threaten public leaks via extortion campaigns (UNC6240).
ShinyHunters may overlap or coordinate with groups like Scattered Spider, especially around the fashion and retail sectors. Both are loosely tied through a criminal network dubbed “The Com”.
Similar Victims With Similar Attack Vector (Salesforce-Linkage is Not Officially Stated)
These organizations have sustained attacks using overlapping TTPs: vishing, OAuth-laden connected app fraud, and help-desk impersonation, matching the Salesforce campaign’s M.O., but without a formal confirmation of Salesforce as the breach vector.
Qantas, UK Retailers (e.g., M&S, Co-op, Harrods), Aviation Giants (KLM, Air France, Hawaiian Airlines, WestJet), Cisco, and Victoria’s Secret.
These entities reported social-engineering-driven breaches targeting CRM-like systems. Many indicated compromised customer service or support platforms, and court documents referenced Salesforce objects like Accounts and Contacts. While not confirmed, the pattern is alarmingly similar to other Salesforce-related incidents.
The Common Thread
Here’s the ugly truth: this wasn’t a Salesforce zero-day. No elite buffer overflow exploit. No kernel-level sorcery.
They used a human zero-day: social engineering, paired with Salesforce’s overly permissive connected app ecosystem and inadequate tenant-level security controls.
The formula was painfully simple:
1. Targeted vishing/phishing: Pretend to be IT, lure employees into granting OAuth permissions to a malicious Salesforce app.
2. Data vacuum: Once connected, attackers could query and exfiltrate everything the user had access to, like customer records, sales pipelines, support histories, and HR files.
3. Pivot: In some cases, access was sold or handed to ransomware crews for monetization.
The real design flaw:
Salesforce’s app ecosystem trusts user-granted OAuth tokens too much, and most organizations have no real-time detection when someone authorizes a new app.
The SaaS Supply Chain Problem
This campaign is Exhibit A in why third-party SaaS vendors are supply chain risks:
- You inherit their attack surface: Their vulnerabilities, their API model, their trust architecture become yours.
- You outsource critical visibility: If the vendor doesn't log granular actions or expose those logs to you in real time, you’re blind.
- One breach = cascading exposure: When attackers breach Salesforce, they’re not hitting just “your account”, they’re exploiting a platform used by 150,000+ other organizations.
How Organizations Using Salesforce Can Protect Themselves?
If you run Salesforce, you’re a target. Period. Here’s how to harden yourself:
- Kill Default App Trust: Disable installation of unverified connected apps. Require admin approval for OAuth scopes.
- Strict Role-Based Access Control (RBAC): Limit who can pull bulk data, export reports, or access sensitive objects.
- Monitor App Authorization in Real-Time: Treat every new connected app like a potential breach.
- Outbound API Monitoring: Watch for unusual API calls, especially bulk queries from unexpected IP ranges.
- Token Hygiene: Revoke unused OAuth tokens periodically.
- Zero Trust for SaaS: Assume your Salesforce is already compromised, and segment data access accordingly.
- Security Awareness Training: No matter how boring it sounds, your people are still the most exploitable surface.
Of course, doing all the above things is not everyone’s cup of tea and could be tedious; that's the reason why we are here at Resonance Security to help you through this. Book a FREE exploration call with us to learn more in detail.
Strategic Takeaways
- Your SaaS vendor is part of your attack surface: Treat them like an internal system, not a “safe cloud”.
- Social engineering will beat tech every time: Salesforce's OAuth model hands attackers the keys if they can trick one human.
- Platform monocultures = systemic risk: When one CRM dominates an industry, one attack vector can harvest dozens of big brands at once.
Final Word
The Salesforce breach wave of 2025 isn’t just a cautionary tale. It’s a systemic warning: the more critical data you centralize in a third-party SaaS, the more you depend on their security architecture, their patch discipline, and their threat intelligence.
When those fail (and they will), you’re not “sharing risk”, you’re inheriting it wholesale.
If you’re still running Salesforce without strict app governance and API monitoring, you’re playing defense in the dark while the attackers have night-vision goggles and a master key.
It’s time to stop assuming that it must be secure by default and start treating every SaaS platform like an insider threat waiting to happen.
If reading this made you uneasy about your own third-party applications setup, good. That’s your wake-up call. At Resonance Security, we don’t just point out risks, we lock them down. From hunting malicious OAuth apps before they drain your data to building airtight SaaS defenses, we make sure your CRM isn’t an open invitation to attackers.
Book your free exploration call today and take back control of your SaaS security.
















.png)