“In crypto, silence is a feature, until it becomes a bug.”
This one has all the ingredients of a Web3 thriller: a top exchange, a notorious hacking crew, a blockchain sleuth throwing shade, and a CEO swatting back accusations. The story of the alleged Crypto.com breach flagged by ZachXBT isn’t just about stolen data; it’s about transparency, trust, and whether regulators and users are being told the whole truth.
Who’s Who in This Drama?
Let’s set the stage.
- Crypto.com is one of the biggest centralized exchanges, known for aggressive growth, global partnerships, and even IPO ambitions.
- Scattered Spider is a hacker collective with a knack for social engineering and phishing; they’ve been linked to SIM swaps, corporate intrusions, and data theft campaigns.
- ZachXBT is the on-chain detective everyone in crypto either fears or loves, depending on which side of his investigations you land. His accusation? Crypto.com suffered multiple breaches and tried to sweep them under the rug.
What The Allegations Say?
According to Bloomberg reports and ZachXBT’s posts, the timeline goes back to 2023. A Crypto.com employee reportedly fell for a phishing attack, with stolen credentials traced back to the chaos around UPS-related leaks. The result: hackers tied to Scattered Spider gained access to internal systems.
The compromise allegedly exposed personal identifiable information (PII) of users. This wasn’t funds directly leaving wallets, but sensitive data: names, contact info, possibly more. The biggest sticking point? Critics claim Crypto.com never properly informed users, instead quietly reporting only to regulators.
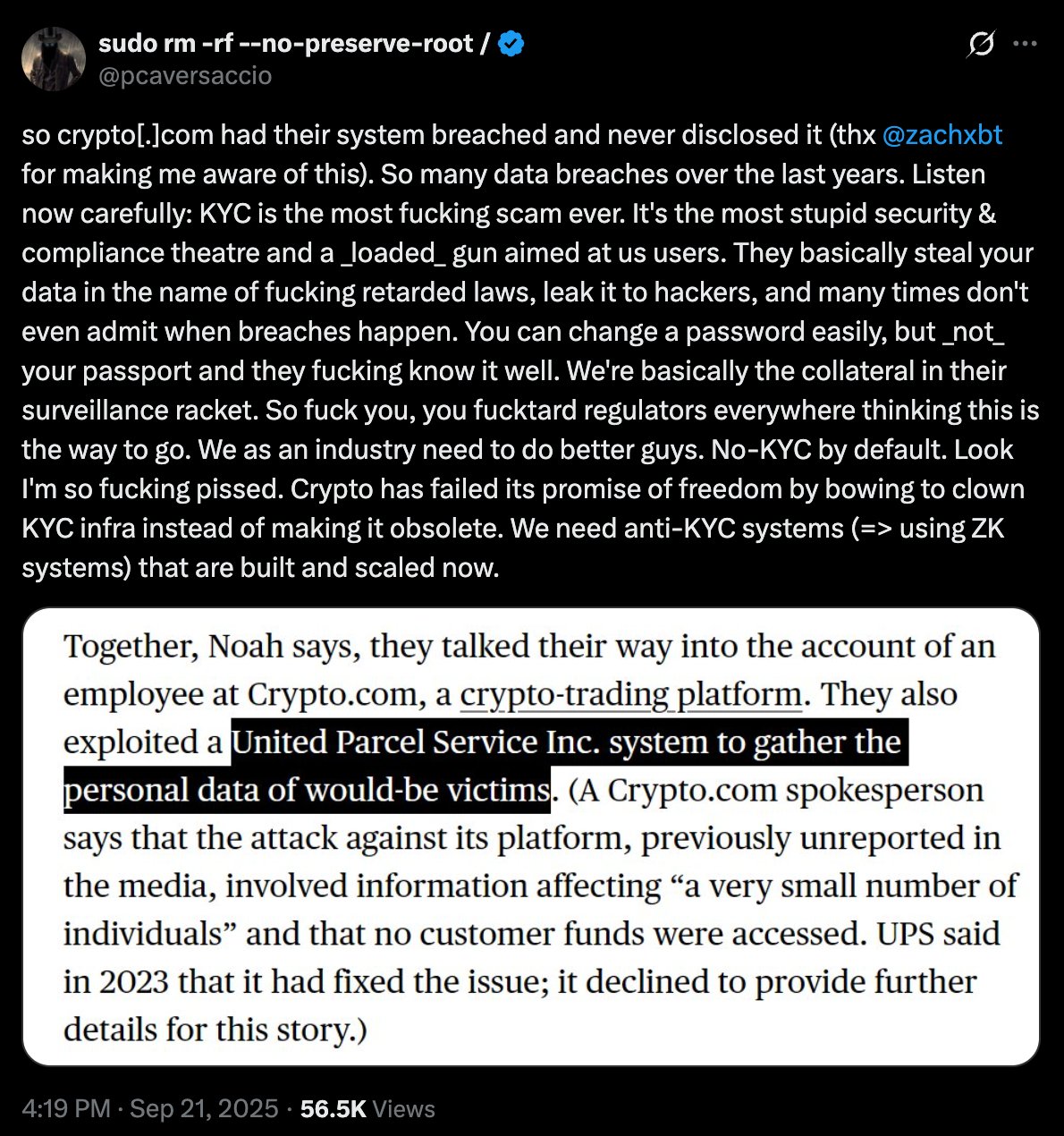
ZachXBT went further, alleging that this wasn’t an isolated slip. In his words, Crypto.com had been “breached several times,” with this just one of the buried skeletons. Whether that’s backed up or still in speculation territory is unclear.
Crypto.com’s Official Line
The company hasn’t denied that something happened. In fact, CEO Kris Marszalek acknowledged the 2023 phishing attempt. But here’s the framing:
- The incident was “limited” in scope.
- Only a very small number of users’ data was exposed.
- No customer funds were touched.
- The breach was detected and contained within hours.
- And most importantly, regulators were notified, including the U.S. Nationwide Multistate Licensing System.

Marszalek called the “cover-up” allegations misinformation, essentially saying: we did our duty, we reported what mattered, and users were never at financial risk.
It’s classic crisis management: admit enough to check the compliance box, deny the bigger narrative, and push the spotlight elsewhere.
The Missing Pieces (Where the Plot Thickens)
Here’s where the questions pile up like unclaimed airdrops:
- What exactly was exposed? Saying “limited PII” could mean just names and emails… or it could mean KYC docs, addresses, and phone numbers. Without detail, we can’t gauge the risk.
- How many users? “Very small number” is corporate-speak. Is that 50 users? 500? 5,000? Nobody outside Crypto.com knows.
- Were users told directly? There’s no solid evidence that affected users got alerts. If the data was sensitive, that silence stings.
- Was this truly just one breach? ZachXBT’s claims of “several breaches” remain unverified, but the doubt lingers.
Why This Isn’t Just Noise?
If you’re thinking, “Well, no funds were stolen, so who cares,” you’re missing the forest for the trees. In crypto, PII is gold for attackers. Exposed phone numbers and emails become SIM swaps. Exposed addresses turn into phishing campaigns. Once tied to KYC, that data is ammunition for full-blown identity fraud.
There’s also the trust factor. Exchanges live and die by reputation. If users feel incidents are downplayed, even if funds are safe, the perception becomes toxic. Add in regulatory expectations around disclosure, and suddenly a “limited” breach can spiral into a governance nightmare.
The Possible Scenarios
There are a few ways to read this story:
- The benign version: It really was tiny. A low-privilege account, minor contact data leaked, regulators looped in, no real harm. Crypto.com’s only sin was not over-sharing.
- The “half-truth” version: Exposure was more serious than admitted, maybe KYC-level data, and while regulators were told, users were kept in the dark to avoid panic.
- The worst-case version: Multiple breaches, higher-level access, and broader PII exposure, and Crypto.com minimized it for reputational reasons.
Which one is true? Depends on how much trust you put in corporate statements versus investigative sleuths.
Lessons For The Rest Of Us
No matter how this shakes out, the playbook is clear for exchanges and projects:
- Don’t rely on phishable MFA. TOTP codes can be stolen. Use WebAuthn/hardware keys for employee accounts.
- Segment employee access. An employee getting phished shouldn’t mean attackers can touch user data. Least privilege isn’t optional.
- Disclose, disclose, disclose. Even if regulators don’t force you, tell your users. Silence kills trust faster than hacks.
- Monitor insider/employee attack vectors. Most “crypto hacks” these days aren’t clever smart contract bugs; they’re social engineering plus weak internal processes.
And for users? Assume your exchange has already been breached once. Use burner emails, compartmentalize your PII, and don’t give attackers an easy pivot from leaked data to your assets.
No Verdict, Just a Question Mark
So, was Crypto.com hiding a massive skeleton, or was this just a molehill blown into a mountain? That’s the million-dollar question. The evidence confirms something happened in 2023. The company says it was tiny and under control. ZachXBT and Bloomberg suggest otherwise.
We’re not here to give you a final verdict; that’s your call. What’s clear is this: even the appearance of secrecy in handling breaches chips away at trust, and in an industry built on fragile reputations, that’s a hack in itself.
How Resonance Security Can Protect Both Companies Like Crypto.com and Users From Phishing?
After studying phishing from AOL’s “You’ve Got Mail” days to today’s Crypto.com phishing attack, and have built some advanced tools to combat advanced phishing attacks.
Introducing:
- Equalizer: Hyper-realistic phishing simulations. No cartoon fishhooks; these mimic real workflows and real lures, forcing people to learn by doing. We believe that if companies start using Equalizer, then they can identify their weak employees and get them educated & trained so that they don’t fall for the real trap.
- PhishGuard (coming soon): An always-on email bodyguard that tells you if the email is safe for you or not, so that even if your email address is leaked in any of the data breaches and hackers try to send you any phishing/malicious emails, PhishGuard flags those emails, keeping you and your $$$ safe.
Book a FREE exploration call to get a gist of our phishing-protection tools.
















.png)