In today’s digital age, phishing attacks have become increasingly sophisticated and prevalent. Cybercriminals employ various tactics to trick unsuspecting individuals into revealing sensitive information or downloading malware. This article aims to raise awareness about this campaign (and many others), shed light on the modus operandi of the attackers, and provide best practices to help users spot fake emails and protect themselves from falling victim to such malicious activities.
Let’s take a look at one active phishing campaign involving impostors posing as Wetransfer, a popular file-sharing service.
The Fake Email
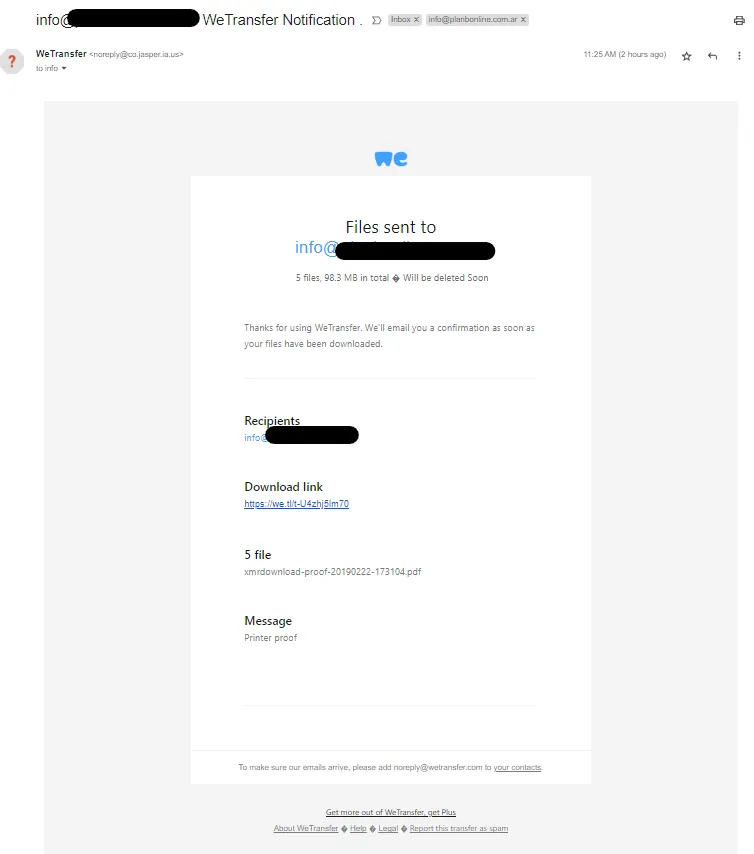
The recent phishing campaign targets users pretending to be from WeTransfer. These fraudulent emails are carefully crafted to appear genuine, luring recipients into downloading malicious files instead of the expected shared content. Cybercriminals exploit the trust associated with WeTransfer’s reputation, often using deceptive subject lines, professional-looking email templates, and legitimate-looking sender addresses.
Spotting Fake Emails: Best Practices
So, when everything appears legitimate at first glance, what should you look for to prevent phishing?
Verify the Sender’s Address
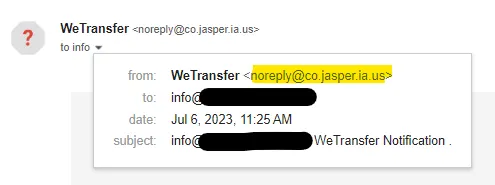
Always double-check the email address of the sender. Phishing emails often mimic legitimate domains, but upon closer examination, you may find small discrepancies or misspellings. Hovering over the sender’s name may reveal a different email address than what is displayed in the visible text. As we can see in this campaign, even though it appears to be from WeTransfer, the actual sender has no connection to them.
Analyze the Email Content
Pay attention to the email’s tone, grammar, and spelling errors. Phishing emails often contain poor grammar, misspelled words, or awkward phrasing. Legitimate companies usually maintain professional standards in their communications.
Be Wary of Urgency and Threats
Phishing emails often create a sense of urgency or fear to prompt immediate action. They may threaten account suspension, claim unauthorized access, or promise exclusive rewards. Take a step back and evaluate the situation calmly before clicking any links or downloading attachments. Or, as in this case, the files will be deleted soon

Check for Personalization
Authentic emails usually address you by name. Phishing attempts often use generic greetings like “Dear Customer” or “Valued User.” Additionally, legitimate companies rarely request sensitive information via email, especially passwords or credit card details.
Scrutinize Hyperlinks and Attachments
Hover your mouse over hyperlinks without clicking to preview the URL. Ensure the destination matches the expected domain and doesn’t redirect to a suspicious or unknown website. Exercise caution when downloading attachments, especially if they prompt you to enable macros or execute files.
On a closer look, we can confirm that the link is not related to WeTransfer.

Another very good recommendation is to run the URL in https://www.virustotal.com

We can check that even though this is an ongoing and new campaign, it was already flagged by at least one vendor.
Avoid Sharing Sensitive Information
Legitimate organizations typically do not request personal or financial information via email. Be cautious if an email asks for sensitive data, such as passwords, Social Security numbers, or banking details. When in doubt, contact the company directly using verified contact information.
Use Multifactor Authentication (MFA)
Enable MFA whenever possible, as it adds an extra layer of security. By requiring additional verification beyond passwords, MFA makes it harder for attackers to gain unauthorized access to your accounts. We specifically recommend hardware MFA like YubiKeys to ensure your most precious assets.
Keep Software Updated
Regularly update your operating system, antivirus software, web browsers, and other applications. Updates often contain security patches that safeguard against known vulnerabilities exploited by cybercriminals.
Educate Yourself and Stay Informed
Stay up-to-date with the latest phishing techniques, security best practices, and common scams. Awareness is your best defense against cyber threats. Educate yourself, share knowledge with others, and encourage a culture of cybersecurity vigilance.
All of the above instructions and processes might look tough and tedious, for individuals, SMBs, startups, and even much more for bigger organizations & institutions. That is why, we at Resonance Security have built Equalizer: An enterprise-grade automated phishing simulation tool, and are building another tool which is an always-on email bodyguard.
Malicious mail detection, seamless phishing simulations, training employees, and much more, made simple for everyone.
Book a FREE demo call with us to get your hands dirty with our phishing-protection tools, because if phishing isn’t part of your defense plan, breach headlines are.
Conclusion
Phishing attacks remain a persistent threat, and cybercriminals are constantly refining their techniques. By familiarizing yourself with the best practices outlined above and remaining vigilant, you can significantly reduce the risk of falling victim to phishing scams. Remember, a momentary lapse in judgment can have a huge impact.
















.png)