Another week (or should say, another weekend), another major crypto breach. This time, one of India’s largest exchanges, CoinDCX, has joined the ever-growing list of centralized platforms targeted by sophisticated attackers. With $44 million drained in a matter of hours, this incident proves yet again that no exchange, no matter how established, is beyond reach.
How the Hack Happened?
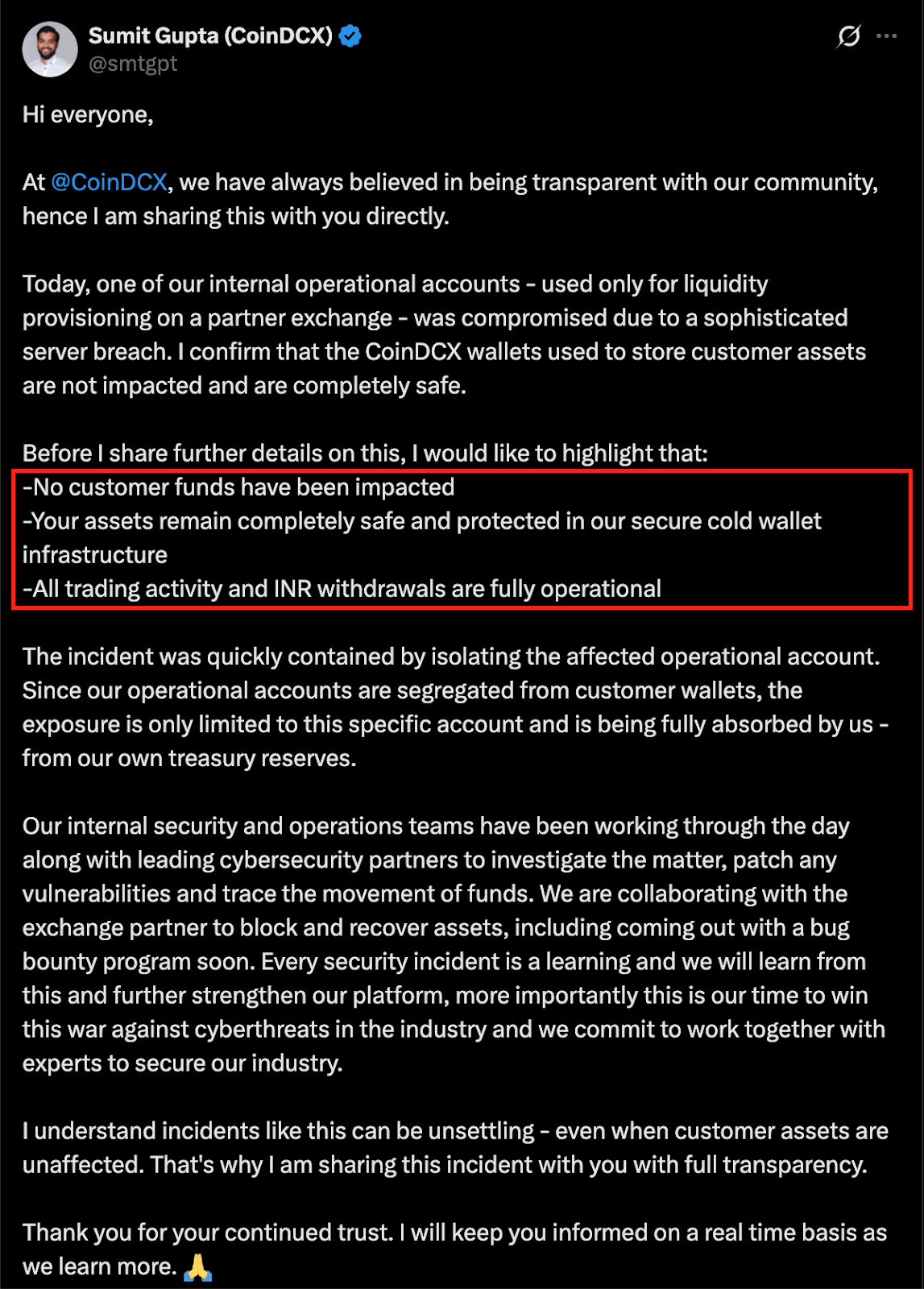
On July 19, 2025, hackers executed a highly targeted attack against CoinDCX’s infrastructure. Unlike typical hot wallet exploits, this breach stemmed from a server-level compromise tied to an internal operational account used for liquidity provisioning on a partner exchange. By breaching this single point, attackers orchestrated the transfer of roughly $44 million across chains, 4,443 ETH (~$15.7M) and 155,830 SOL (~$27.6M), before routing the funds through bridges and privacy mixers to obscure their trail.
Crucially, no customer assets were stolen. CoinDCX confirmed that the entire loss will be covered by its treasury, and core INR trading and withdrawals continued to function throughout the incident.
The Controversy: Delay and Damage Control
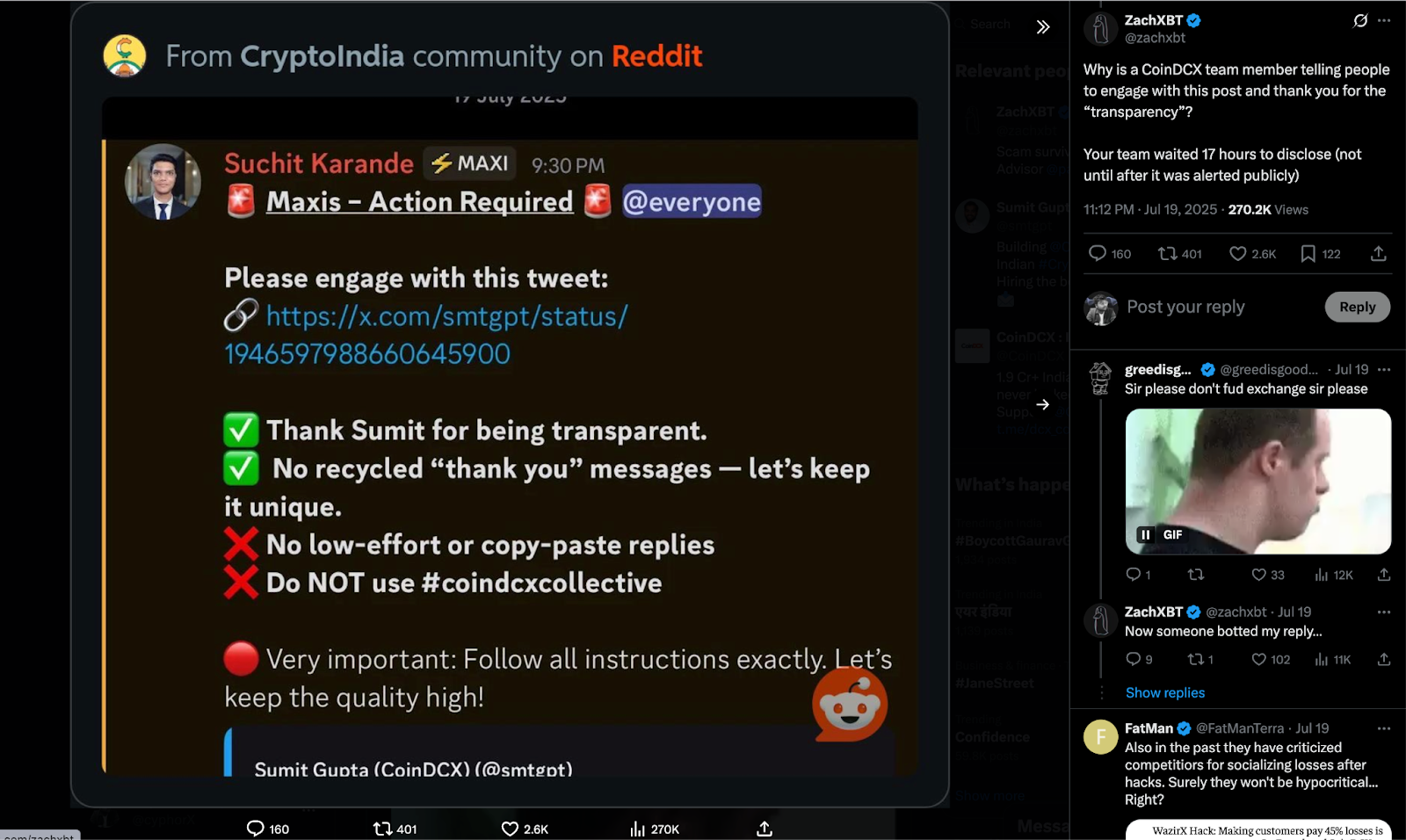
While the breach itself was significant, the fallout wasn’t just about the money. CoinDCX reportedly took 17 hours to publicly acknowledge the hack, a delay that raised concerns about transparency during active attacks.
Adding fuel to the fire, multiple reports across crypto forums allege that CoinDCX mobilized its internal network and influencers to flood social channels with praise, downplaying criticism and amplifying narratives about their “transparent, swift and professional” response. Critics argue this was more about optics than accountability.
Some industry insiders also questioned why such a large operational account was left so exposed and why no multi-sig or transaction throttles were in place to prevent a single breach from escalating to $44 million in losses.
Lessons from the CoinDCX Breach
Internal Systems Are Not Immune
Even accounts considered “operational” can become high-value targets. Zero-trust principles must extend to all accounts, whether internal or external.
Bridges Are a Laundering Playground
Once funds hit cross-chain bridges and mixers, tracing becomes a nightmare. Monitoring and setting triggers for bridge transactions is critical.
Response Defines Reputation
CoinDCX’s quick containment, continued operations, and full reimbursement commitment demonstrate how effective crisis management can preserve user trust even after a multimillion-dollar breach.
Infrastructure Hardening Is Non-Negotiable
Server security, network segmentation, and strict access controls aren’t optional; they’re baseline requirements in 2025.
How Similar Exchanges Can Stay Secure
Establish and Maintain Multi-Sigs
Implementing a multi-sig for operational accounts enhances internal security and its beneficial for shared accounts, like corporate treasuries, where multiple parties need to agree on financial actions.
Harden Internal Infrastructure
Use zero-trust frameworks, hardened operating systems, and network isolation for all operational accounts.
Deploy Real-Time Monitoring
Detect unusual fund flows, especially large transactions through bridges, before attackers vanish.
Segment Operational Functions
Isolate liquidity accounts with strict permission limits and multi-sig requirements to reduce blast radius.
Implement Bridge Risk Controls
Use transaction delays, limits, and anomaly alerts for cross-chain operations.
Maintain Reserves and Transparency
Be prepared to cover losses instantly, and communicate openly to retain market confidence.
Engage External Forensics & Bug Bounties
Proactively identify and patch weaknesses before attackers do.
Final Word: Security Is Strategy
The CoinDCX hack is more than another line in 2025’s growing breach list; it’s a case study in how quickly sophisticated actors can penetrate, extract, and vanish, and how exchanges must be prepared to handle the fallout.
But it’s also a reminder: real trust comes from transparency, not PR spin. Prevention is ideal, detection is essential, but response (genuine and fast) is everything. In today’s crypto landscape, security isn’t just about firewalls and audits; it’s about resilience, readiness, and the courage to be honest when things go wrong.
At Resonance Security, we help projects fortify their infrastructure with our suite of offensive simulations, continuous monitoring, and real-time detection tools. If you’re building cross-chain vaults, AMMs, exchanges, lending protocols, or anything else related to crypto & web3, now is the time to take security seriously.
Book a FREE exploration call to discuss further with us how we can help you.
Stay secure, or become the next headline.
About the Author
Rhythm Jain is the Marketing Development Manager at Resonance Security, bringing several years of experience in marketing and business development. As a cybersecurity enthusiast turned marketing professional, he specializes in crafting strategies that amplify brand presence and drive user engagement across web2 and web3 ecosystems.
















.png)